Cross Site Scripting - Level 05 __ Frozen Flame
var x = "I am not HTML";
Hello thirsty learners. Till this blog, we were talking about Cross Site Scripting Attack in HTML context. But, now, we will talk about " JavaScript " context. That's why I named this blog, " I am not HTML ". So, let's start hacking..
I was going through a website. And, I found something interesting there. What I was writing my payload, it was reflecting but, inside the <script>...</script> tag. If we use the HTML context and, give the html vectors like, svg, img etc, the XSS won't trigger at all. In this case, we have to think like, JavaScript.
Exploitation ::
When I gave input to a particular param, it was reflecting in the source code. But, in the script tags. So, I tried to close the </script> tag. But , the payload was getting filtered. It was looking like this,
Well, that means, we can't close the tags. So, we have to think different here.
Same Scenario ::
Scenario 1 ::
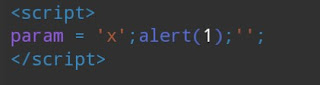
If your payload in inside ( ' ) like this ,
Then, use this payload , ';alert(1);'
Scenario 2 ::
If the semicolon ( ; ) gets filtered by the web application or the filter, use like these methods ::
'-alert(1)-'
'+alert(1)+'
Scenario 3 ::
Happy Hacking. 💥